参考
http://blog.csdn.net/kafeiflynn/article/details/6429976
1.systemtap脚本以.stp为扩展名,其基本格式如下
probe event{statements}
2.可以用*来代表通配符
probe kernel.function("*@net/socket.c"){ }
probe kernel.function("*@net/socket.c").return{ }
代表了所有net/socted的入口和出口
3.可以测试跟踪模块
probe module("pcmfs").function("*").call{
...}
probe module("pcmfs").function("*").return{
...}
4.下面以及各例子说明
例1:ext4.stp
#!/usr/bin/stap
probe kernel.function("*@fs/ext4/namei.c"),
kernel.function("*@fs/ext4/namei.c").return,
kernel.function("*@fs/ext4/ialloc.c"),
kernel.function("*@fs/ext4/ialloc.c").return
{
printf("PID:%d probepoint : %s execname: %s\n",pid(),pp(),execname());
}
第一行#!/usr/bin/stap 为像系统指定该脚本的类型stap。改程序probe监控四个事件,当这四个时间发生时, 打印改行:printf("PID:%d probepoint : %s execname: %s\n",pid(),pp(),execname());
其中pid为进程号,pp()可以打印 函数名,该函数所在的具体目录具体地点的行数,execname为
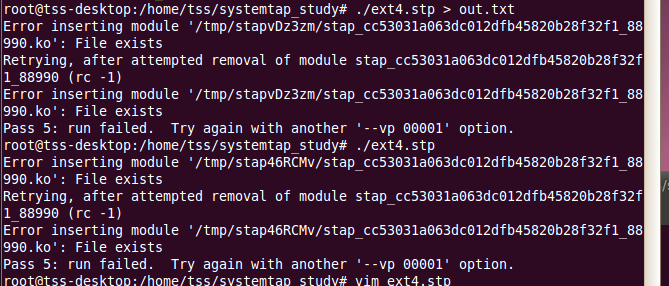
chmod +x ext4.stp变为可执行文件,然后./ext4.stp运行该脚本。在另一个终端输入:mkdir newdir则可以看到函数调用结果:
root@desktop:/home/systemtap_study# ./ext4.stp
PID:3020 probepoint : kernel.function("ext4_lookup@fs/ext4/namei.c:1054") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_find_entry@fs/ext4/namei.c:876") execname: mkdir
PID:3020 probepoint : kernel.function("search_dirblock@fs/ext4/namei.c:826") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_find_entry@fs/ext4/namei.c:876").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_lookup@fs/ext4/namei.c:1054").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_mkdir@fs/ext4/namei.c:1827") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_update_dx_flag@fs/ext4/namei.c:800") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_new_inode@fs/ext4/ialloc.c:788") execname: mkdir
PID:3020 probepoint : kernel.function("find_group_orlov@fs/ext4/ialloc.c:460") execname: mkdir
PID:3020 probepoint : kernel.function("get_orlov_stats@fs/ext4/ialloc.c:414") execname: mkdir
PID:3020 probepoint : kernel.function("get_orlov_stats@fs/ext4/ialloc.c:414").return execname: mkdir
PID:3020 probepoint : kernel.function("find_group_orlov@fs/ext4/ialloc.c:460").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_claim_inode@fs/ext4/ialloc.c:709") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_read_inode_bitmap@fs/ext4/ialloc.c:101") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_read_inode_bitmap@fs/ext4/ialloc.c:101").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_new_inode@fs/ext4/ialloc.c:788").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_set_de_type@fs/ext4/namei.c:1126") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_next_entry@fs/ext4/namei.c:210") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_set_de_type@fs/ext4/namei.c:1126") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_add_entry@fs/ext4/namei.c:1474") execname: mkdir
PID:3020 probepoint : kernel.function("add_dirent_to_buf@fs/ext4/namei.c:1290") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_match@fs/ext4/namei.c:813") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_from_disk@fs/ext4/namei.c:182") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_rec_len_to_disk@fs/ext4/namei.c:191").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_set_de_type@fs/ext4/namei.c:1126") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_update_dx_flag@fs/ext4/namei.c:800") execname: mkdir
PID:3020 probepoint : kernel.function("add_dirent_to_buf@fs/ext4/namei.c:1290").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_add_entry@fs/ext4/namei.c:1474").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_inc_count@fs/ext4/namei.c:1708") execname: mkdir
PID:3020 probepoint : kernel.function("ext4_inc_count@fs/ext4/namei.c:1708").return execname: mkdir
PID:3020 probepoint : kernel.function("ext4_mkdir@fs/ext4/namei.c:1827").return execname: mkdir
上述一个mkdir的动作就调用了许多函数,如果需要看特定一个函数,可以通过管道再使用grep查找
例二:将进出函数的退出函数分开标记
#!/usr/bin/stap
probe kernel.function("*@fs/ext4/file.c"),
kernel.function("*@fs/read_write.c"),
kernel.function("*@fs/ext4/namei.c"),
kernel.function("*@fs/ext4/ialloc.c")
{
ts = __indent_timestamp()
t1=gettimeofday_ms
printf(">>>>>>%d %6d PID:%d probepoint : %s execname: %s\n",t1,ts,pid(),pp(),execname());
}
probe kernel.function("*@fs/ext4/file.c").return,
kernel.function("*@fs/read_write.c").return,
kernel.function("*@fs/ext4/ialloc.c").return,
kernel.function("*@fs/ext4/file.c").return
{
printf("<<<<<<PID:%d probepoint : %s execname: %s\n",pid(),pp(),execname());
}
例三:用strace来跟踪
这里不是采用的systemtap,而是strace。其中./blktrace为运行程序名字。output.txt为输出文件名。
#!/bin/sh
strace -o output.txt -T -tt -e trace=all ./blktrace_study
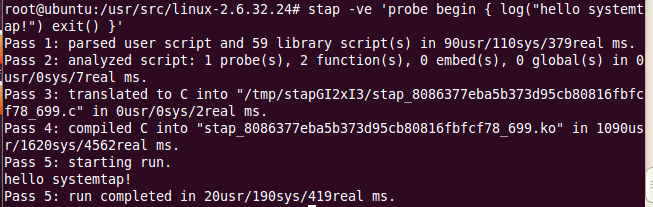 下类似的输出结果:
下类似的输出结果: